Guard-en Party Summary
From March 26th through April 2nd 2022, the Data Platforms Engineering and Architecture (DPEA) team, Security Assurance and Research (DSAR) team collaborated with Intel Product Assurance and Security (IPAS), the Intel® SGX team, and an external vendor named Intigriti held the Guard-en Party under the umbrella of IPAS’ bug bounty program called Project Circuit Breaker. Intigriti continues to be a key partner in enabling Intel to connect with external researchers in the security community and provided logistical assistance for the event. There were two key objectives for Guard-en Party: identify qualified researchers for the Intel® TDX campaign and live-test our Intel® DevCloud infrastructure and support capabilities for use with external researchers. Project Circuit Breaker sought applications from the researcher community to participate in the Party. A total of 103 applied, 14 were selected, and 10 researchers participated in a training-style event. Participants worked directly with renowned security researchers and Intel experts to learn about Intel® SGX technology. This “capture the flag” type event included some hand-crafted vulnerable applications that participants were asked to exploit using the tools, techniques, and skills presented during the training sessions.
The Guard-en Party event was successfully completed. Two qualified security researchers were selected for the Intel® TDX campaign with an additional two on the waitlist. Intel® DevCloud infrastructure and support has been thoroughly exercised to ensure smooth execution of the Intel® TDX campaign.
Objectives & Goals
The key objectives & goals for the Guard-en Party bug bounty event were:
- Develop a proof-of-concept event leveraging Intel® SGX technology in preparation for the Intel® TDX campaign.
- Stress test Intel® DevCloud processes around using the environment, setup, support, and staffing.
- Introduce Project Circuit Breaker to a new audience who had not engaged with the Intel® Bug Bounty Program before and develop a strong relationship with them.
- Identify and recruit new researchers with the required skill set and form new relationships with members of the researcher community who specialize in techniques that are likely to find vulnerabilities in Intel® TDX.
- Establish event execution plan for Intel specific training and development events.


Outreach, Planning, & Programming
In early February, the Intigriti team worked with Project Circuit Breaker to promote the Guard-en Party event across multiple outreach channels. The response was excellent. Overall, we received over 103 applications from across the world. Of the 103, 25 were deemed qualified for the event. The top 14 applicants were invited to the event and the other 11 were waitlisted. Selected participants were screened against sanctions and restricted party lists.
Upon receiving their invitations to the event, confirmed researchers were sent promotional packages from both Project Circuit Breaker and the Intigriti team. The event was divided across two weekends and one full week – March 26th through April 2nd. This was a virtual event conducted over Zoom platform and all the sessions were recorded. Recordings were made available to event participants for the duration of the event only.
Saturday, March 26th
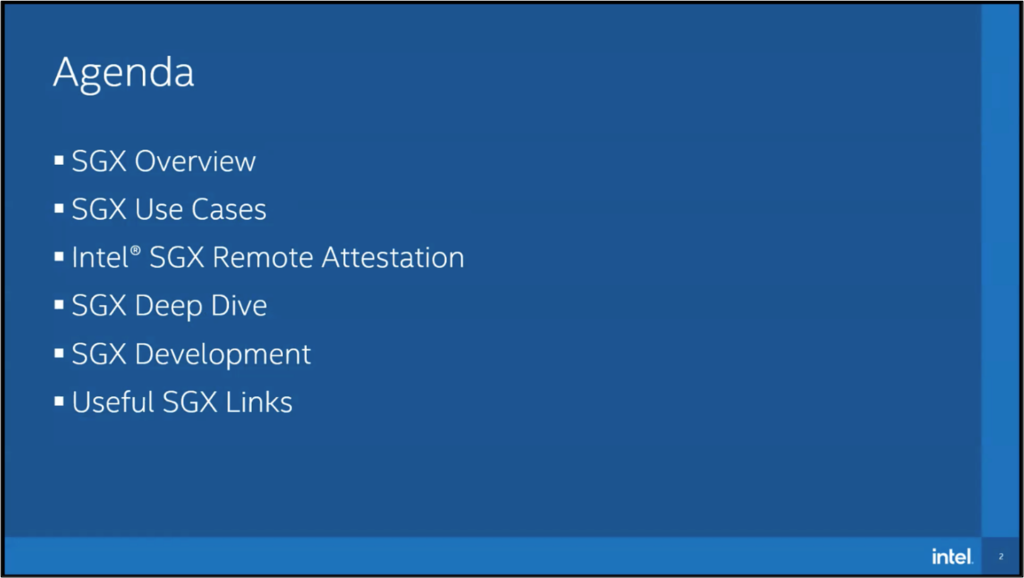
Intel® SGX Overview
Hacker Trivia
Intel® DevCloud Walkthrough and Setup
Sunday, March 27th
Researcher Introductions & Ice Breaker
Guest speaker – Jo Van Bulck – KU Leuven
Intel® SGX Proof of Concept (POC) Walkthroughs
Monday, March 28th – Friday, April 1st
Researchers found hypothetical vulnerabilities in the POCs and submitted reports via the Intigriti platform
Saturday, April 2nd
Show & Tell – The top two reports were selected by the Intel team and each researcher shared their strategies, techniques, and learnings with the group.
POC Walkthroughs – Intel engineers walked through each POC and the logic behind them and what they were looking for.
Event wrap-up
Technical Details
Researchers were provided with two proofs of concept applications to explore and exploit which were developed using known exploitable coding techniques. Each POC consisted of a simple application and an Intel® SGX enclave with bugs. The objective for each researcher was to find and describe the bugs in the Intel® SGX enclave, mechanism to exploit the bugs, and develop functional exploits.
Researchers were provided with descriptions of the applications that included hints for each POC’s hypothetical vulnerability(ies).
Lessons Learned
Overall, the event was a success, and all objectives and goals were met. Lessons learned for future events include, but are not limited to:
Organization & Planning
- Develop and share tools and templates for continued collaboration.
- Get agendas and bounty tables at least one week in advance, so that participants can be more prepared and understand expectations and time commitments.
- It took us a considerable amount of time to define the nature of Intel® SGX We came to a point where it was about to be abandoned. Organizers need to make sure we define scope much faster.
- Develop long term documents that can be used regularly for each Project Circuit Breaker event. This includes shared secure folders and storage.
- We would have liked the POCs and hints to be ready earlier to ensure time for internal review and testing, ideally 2-6 weeks.
Execution & Engagement
- Social activities go a long way for relationship building – icebreakers and non-technical activities should continue to grow, especially for virtual events.
- For future training events, consider extending them longer than one week as some researchers have requested more time to work on the exercises.
- Show & Tell continues to thrive as a key component for events – virtual or in person.
Post-Event Activities
- As new vulnerabilities are submitted, consider if they could be turned into a CTF-style challenge that can be packaged and re-used in a future training-style event. This will require significant engineering effort with appropriate planning.
- Add writeups from researchers, interviews/video content, recordings of anything we can share, descriptions of the challenges, etc. to the Project Circuit Breaker website so other people can participate on their own outside of the event.
Results Achieved

Live test of Intel® DevCloud infrastructure and support capabilities for use with external researchers
Success with improvement opportunities

Identify qualifies researchers for Intel® TDX bug bounty on Eagle Stream
Success – 4 individuals identified (2 invited, 2 waitlisted)

Identify areas of improvement to prepare for Intel® TDX campaign
Achieved – details captured in see Lessons Learned section